Welcome to CXQuest, where we explore the cutting-edge innovations transforming customer experience and cybersecurity landscapes. Today’s conversation centers on a critical evolution in enterprise security – the shift from traditional network fortification to human-centered defense strategies. Our guest today is Govind Rammurthy, CEO and MD, eScan.
As we navigate an increasingly complex digital threat environment, organizations worldwide are discovering that their most sophisticated firewalls and multi-factor authentication systems can be rendered ineffective by a single convincing email. The cybersecurity industry is experiencing a paradigm shift, where artificial intelligence isn’t just defending networks – it’s also being weaponized to create phishing campaigns of unprecedented sophistication and scale.
Our discussion today with Govind focuses on eScan XDR’s groundbreaking response to this challenge: a comprehensive phishing simulation platform that prepares employees for the next generation of AI-powered social engineering attacks. This isn’t merely another security tool – it represents a fundamental reimagining of how organizations build resilience against threats that operate at machine speed with human-like persuasion.
Cybercriminals Leveraging Generative AI
The stakes couldn’t be higher. Recent threat intelligence reveals that cybercriminals are leveraging generative AI to create phishing content that can mimic corporate tone, reference internal jargon, and adapt to industry-specific language within seconds. We’re witnessing targeted campaigns that spoof venture capital funding offers to fintech startups and personalized job offers that fool HR departments – attacks that demonstrate how the traditional boundaries between automated and human-crafted deception have completely dissolved.
What makes this conversation particularly relevant is the recognition that perfect prevention is no longer a realistic goal. Instead, the focus must shift toward building organizational immunity through controlled exposure and continuous learning. eScan XDR’s approach acknowledges that cybersecurity has evolved from a technical challenge to a language game, where the quality of human judgment becomes the final line of defense.
Today, we’ll explore how this innovative platform addresses the growing sophistication of phishing attacks, the psychology behind effective security training, and the broader implications for customer experience teams who must balance security protocols with seamless user interactions. We’ll examine how organizations can build cultures of security awareness that don’t impede productivity, and discuss the metrics that matter when measuring human-centered cybersecurity effectiveness.
The Threat Landscape Evolution
Q1. Can you walk us through how the phishing threat landscape has fundamentally changed with the introduction of generative AI tools? What specific examples have you observed that demonstrate this shift from traditional to AI-powered attacks?
GR: The shift is dramatic or, I can say, drastic. Traditional phishing relied on mass distribution with obvious tells – poor grammar, generic greetings, suspicious links, poor images, and bad alignment. Now, attackers use AI to generate personalized content at scale.
We’ve seen campaigns where attackers scraped executive LinkedIn profiles to craft convincing internal emails, complete with company-specific terminology and current project references. The speed has changed too – what once took weeks of research now happens in minutes.
Beyond Traditional Security
Q2. With corporate networks becoming increasingly fortified through MFA and biometric systems, why are cybercriminals finding human psychology to be their most effective attack vector? How does this change the security conversation for CX leaders?
GR: Technology barriers force attackers toward the path of least resistance – people. Traditionally, humans have always been the weakest link when it comes to security! Put the best of locks and forget to close the window! Ironical, but true.
You can’t brute-force a retina scanner, but you can convince someone to share credentials through a believable scenario. For CX leaders, this means shifting from purely technical defenses to understanding behavioural patterns. Security becomes less about building walls and more about teaching people to recognize manipulation tactics in real-time communication.
It is like teaching a child not to accept things from strangers or not to get into a conversation with a stranger.
The Psychology of Deception
Q3. What makes modern AI-generated phishing attempts so convincing compared to the obvious spelling errors and suspicious links we used to see? How do these attacks specifically target the cognitive shortcuts that busy employees rely on?
GR: AI-generated content mimics authentic communication patterns perfectly – correct grammar, appropriate tone, relevant context. These attacks exploit cognitive shortcuts like authority bias and urgency response. This is natural because AI has been trained using genuine communications.
When someone receives what appears to be a legitimate request from their CEO about an urgent client matter, they process it quickly rather than scrutinizing details. The attacks are designed to trigger fast decisions, bypassing critical thinking.
Simulation vs. Reality
Q4. How does your phishing simulation platform differ from traditional security awareness training? What makes controlled exposure more effective than periodic training sessions?
GR: Traditional training is like learning to swim by reading about water. Our platform creates actual scenarios employees will face, letting them experience the pressure of realistic attacks in a safe environment. Controlled exposure builds muscle memory – when someone encounters a real attack, they’ve already navigated similar situations. It’s continuous skill-building rather than information dumping, which research shows is far more effective for retention.
Measuring Human Security
Q5. What metrics do you track to assess the effectiveness of phishing simulation training? How do you balance identifying vulnerabilities with maintaining employee trust and morale?
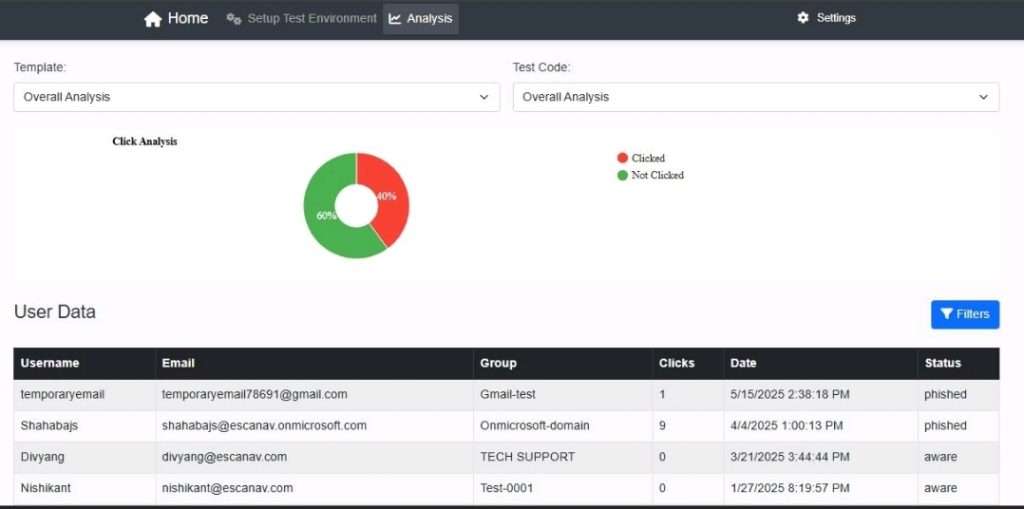
GR: We track click rates, reporting behaviour, and time-to-recognition across different attack types. The key is framing this as skill development, not “hey, we caught you!” moments. We focus on improvement trends rather than individual failures, celebrating employees who report suspicious emails even if they initially clicked. The goal is to build confidence in decision-making, not creating fear of making mistakes during the learning process.
Industry-Specific Targeting
Q6. You mentioned attacks targeting European fintech startups with fake VC offers and HR departments with job proposals. How does your platform adapt to industry-specific threat patterns?
GR: Our platform draws from current threat intelligence to create industry-relevant scenarios.
For fintech, we simulate investment scams and regulatory compliance requests. For healthcare, we focus on patient data requests or insurance verification. The system learns from actual attack patterns reported across our network, ensuring training scenarios match what employees in specific sectors encounter in their daily work.
The Customer Experience Impact
Q7. For CX professionals, security measures often create friction in customer journeys. How can organizations implement robust phishing defense without compromising user experience?
GR: The key is making security invisible to legitimate users while catching malicious attempts. Our approach focuses on employee (or should we say team member) behavior rather than adding customer-facing verification steps. When employees can better identify threats, you need fewer intrusive security measures for customers. Good phishing defense improves customer experience by preventing the disruptions that come with successful attacks and subsequent incident response.
Real-Time Adaptation
Q8. How does your platform incorporate current threat intelligence to ensure employees are training against the types of attacks they’re most likely to encounter?
GR: We continuously update our scenario database based on live threat feeds and attack patterns observed across our customer base. When a new phishing technique emerges, like fake Microsoft Teams notifications or AI-generated voice messages – we quickly develop training simulations. This ensures employees aren’t just prepared for yesterday’s attacks, but for the evolving tactics they’ll actually face next week.
Organizational Culture
Q9. What role does organizational culture play in building effective phishing defense? How do you foster a security-aware culture without creating a climate of fear or suspicion?
GR: Culture is everything. If employees fear punishment for reporting suspicious emails or admitting mistakes, they’ll stay silent when attacks succeed. We help organizations and cybersecurity team members create environments where security awareness is viewed as an important skill, not a burden. When possible, we also suggest recognition programs for good security behavior and transparent discussion of near-misses to ensure overall contribution to a positive security culture.
Integration Challenges
Q10. How does your simulator integrate with existing security infrastructure? What considerations should CX teams have when implementing these systems alongside customer-facing platforms?
GR: Integration happens through standard APIs with existing email security and incident response platforms. For CX teams, the main consideration is ensuring simulation emails don’t interfere with customer communications or support workflows. We provide clear tagging and scheduling controls to avoid sending simulations during critical customer interactions or high-stress periods.
The Language Game
Q11. You’ve described modern cybersecurity as evolving from a “numbers game” to a “language game.” Can you elaborate on what this means for security strategy and employee training?
GR: Previously, attackers sent millions of obvious phishing emails, hoping a small percentage would succeed. Now they design fewer, highly targeted messages (kind of spear phishing) that look completely legitimate. Hence, defense strategies also must shift from catching obvious threats to detecting subtle manipulation.
Almost all training that you see on Internet sites asks you to look at suspicious links (look for lock symbol or https before URL, etc). But now training needs to focus on communication analysis – tone, context, timing rather than just looking for technical red flags like suspicious links.
Future-Proofing Defense
Q12. As AI capabilities continue advancing, how do you anticipate phishing attacks will evolve? What strategies can organizations implement now to prepare for threats we haven’t seen yet?
GR: We’re already seeing voice cloning and video deepfakes in social engineering. Future attacks will combine multiple AI-generated elements – voice, video, and text – to create completely convincing scenarios. Organizations should focus on verification protocols (verify using an alternate channel) that don’t depend solely on communication authenticity. Building processes for confirming unusual requests through independent channels needs to be kept in place.
ROI and Business Impact
Q13. From a business perspective, how do organizations measure the return on investment for phishing simulation platforms? What cost factors should CX leaders consider?
GR: ROI typically shows up as reduced incident response costs and avoided business disruption. A single successful phishing attack can cost lakhs or crores in remediation, fines, and customer trust damage. The platform cost is minimal compared to those risks. CX leaders should factor in customer retention benefits – customers trust organizations that demonstrate strong security practices and haven’t experienced embarrassing data breaches.
Cross-Departmental Collaboration
Q14. How can security teams better collaborate with customer experience teams to ensure security measures enhance rather than hinder customer relationships?
GR: The best collaboration happens when both teams understand that security incidents damage customer relationships far more than security measures do. Regular communication about threat landscape changes helps CX teams understand why certain protections are necessary. Internal security teams should involve CX in rolling out customer-facing security processes, ensuring they feel protected to legitimate customers.
Global Implementation
Q15. What challenges do multinational organizations face when implementing phishing simulation training across different cultures and languages? How does your platform address these complexities?
GR: Cultural communication norms vary significantly – what seems urgent in one culture might seem rude in another. Our platform includes region-specific scenarios that account for local business practices, holidays, and communication styles. We also provide multilingual support and work with local team members to ensure training scenarios feel authentic rather than like obvious translations. Without a doubt, cultural sensitivity is crucial for effectiveness when it comes to security training.
Closing
As we conclude today’s exploration of AI-powered phishing defense, several key insights emerge that will shape how organizations approach cybersecurity in the coming years. The conversation with Govind Rammurthy, CEO and MD, eScan XDR has illuminated a fundamental truth: the future of enterprise security lies not in building higher walls, but in developing more sophisticated human judgment.
The shift from traditional network fortification to human-centered defense strategies represents more than a tactical adjustment – it’s a recognition that cybersecurity has become fundamentally about understanding and improving human behavior under pressure. As artificial intelligence democratizes the creation of convincing deception, the ability to spot subtle inconsistencies, verify unusual requests, and maintain healthy skepticism becomes invaluable organizational capabilities.
For customer experience professionals, this evolution presents both challenges and opportunities. The challenge lies in implementing security measures that don’t create friction in customer journeys or erode trust in digital communications. The opportunity exists in recognizing that security-aware customers are often more engaged and loyal customers, particularly in industries where data protection directly impacts consumer confidence.
Metrics That Matter
The metrics that matter in this new landscape extend beyond traditional technical indicators. Click-through rates, reporting behaviors, and cross-departmental vulnerability patterns provide insights not just into security posture, but into organizational culture, communication effectiveness, and employee engagement. These human-centered metrics offer CX leaders valuable data about how their teams process information, respond to pressure, and maintain vigilance in routine operations.
Perhaps most significantly, today’s discussion highlights how the concept of “perfect prevention” is giving way to “adaptive resilience.” Organizations that thrive in this environment will be those that view security incidents as learning opportunities rather than failures, that invest in continuous training rather than periodic compliance exercises, and that recognize cybersecurity as a shared responsibility rather than an IT department concern.
The integration of phishing simulation platforms with existing customer experience infrastructure also points toward a future where security and usability converge rather than compete. As these systems become more sophisticated, they offer the potential to enhance rather than impede customer interactions by building more trustworthy, reliable digital environments.
Looking Ahead
Looking ahead, the implications extend far beyond email security. The same principles that make phishing simulation effective – controlled exposure, realistic scenarios, continuous adaptation, and behavioral analytics – apply to broader challenges in customer education, employee development, and organizational change management. CX leaders who embrace these human-centered security approaches may find themselves with valuable insights applicable across their entire customer journey optimization efforts.
The conversation around AI-powered phishing defense ultimately reflects larger questions about how humans and artificial intelligence will coexist in professional environments. As AI capabilities expand, the uniquely human skills of pattern recognition, contextual judgment, and intuitive skepticism become more valuable, not less. Organizations that invest in developing these capabilities through platforms like eScan XDR’s simulator are not just preparing for current threats – they’re building foundational skills for navigating an increasingly complex digital future.
For CXQuest listeners, the takeaway is clear: the future belongs to organizations that can seamlessly blend technological sophistication with human wisdom, creating experiences that are both secure and seamless, both protective and productive. The companies that master this balance will not only defend against today’s threats but will build competitive advantages that extend far beyond cybersecurity into every aspect of customer experience and organizational effectiveness.
Thank you for joining us for this deep dive into the evolving landscape of cybersecurity and customer experience. As always, we encourage you to continue the conversation and share your own insights on how your organization is adapting to these emerging challenges and opportunities.