When Your Security Operations Center Becomes Your Customer Experience Blind Spot
Picture this: A customer tries to complete a transaction. Your security systems flag it as suspicious. The alert sits in a queue with 10,000 others. By the time an analyst investigates, the customer has abandoned their cart and tweeted their frustration. This scenario plays out thousands of times daily in organizations worldwide.
Security operations centers were built to protect the business. But when SOC teams drown in alerts, burn out from overwork, and struggle with outdated tools, they inadvertently create friction that damages customer and employee experiences alike.
The connection between security operations and experience management isn’t obvious until something breaks. Then it becomes painfully clear.
The Hidden CX Cost of Legacy Security Operations
Security teams face an impossible equation. Cyber threats grow exponentially while budgets stay flat. The global cybersecurity skills gap has reached 4.8 million unfilled positions. Meanwhile, 62% of cybersecurity leaders report experiencing burnout, with 44% suffering multiple episodes throughout their careers.
This workforce crisis directly impacts customer experience. Overworked analysts make mistakes. Alert fatigue causes real threats to slip through. Response times slow to a crawl.
When a major private bank processes over 1.3 million security events per second, manual triage becomes impossible. False positives overwhelm teams. Legitimate customer activities get blocked. Trust erodes one bad experience at a time.
The customer never sees the exhausted analyst reviewing their 50th false positive of the hour. They only experience the declined transaction, the locked account, or the delayed service.
Why Traditional SIEM Approaches Fail Both Security and Experience
Legacy security information and event management systems create as many problems as they solve. They collect everything but analyze little. Storage costs spiral out of control. Teams spend more time managing the SIEM than investigating threats.
Organizations face a brutal choice: ingest all data and pay crushing licensing fees, or exclude potentially valuable logs and risk blind spots. Both paths lead to suboptimal outcomes.
Traditional SIEMs treat all logs equally. Firewall noise sits alongside critical authentication failures. Analysts wade through irrelevant alerts to find genuine threats. This approach wastes time, money, and analyst patience.
The impact cascades beyond the SOC. When security teams can’t distinguish signal from noise, they implement overly aggressive controls. Legitimate customers get caught in security nets designed for criminals. Employees face friction accessing the tools they need to serve customers effectively.
According to research, organizations with effective SIEM solutions detect threats up to 50% faster than those without. But effectiveness depends on implementation quality, not just deployment.
The Securonix Recognition: What Gartner’s Assessment Reveals
Securonix’s placement as a Leader in the 2025 Gartner Magic Quadrant for SIEM marks their sixth consecutive year in this position. This recognition, combined with their Customers’ Choice designation in Gartner Peer Insights, reveals something important about the evolution of security operations.
The market is rewarding vendors who solve real operational challenges. Not just those who pack in features.
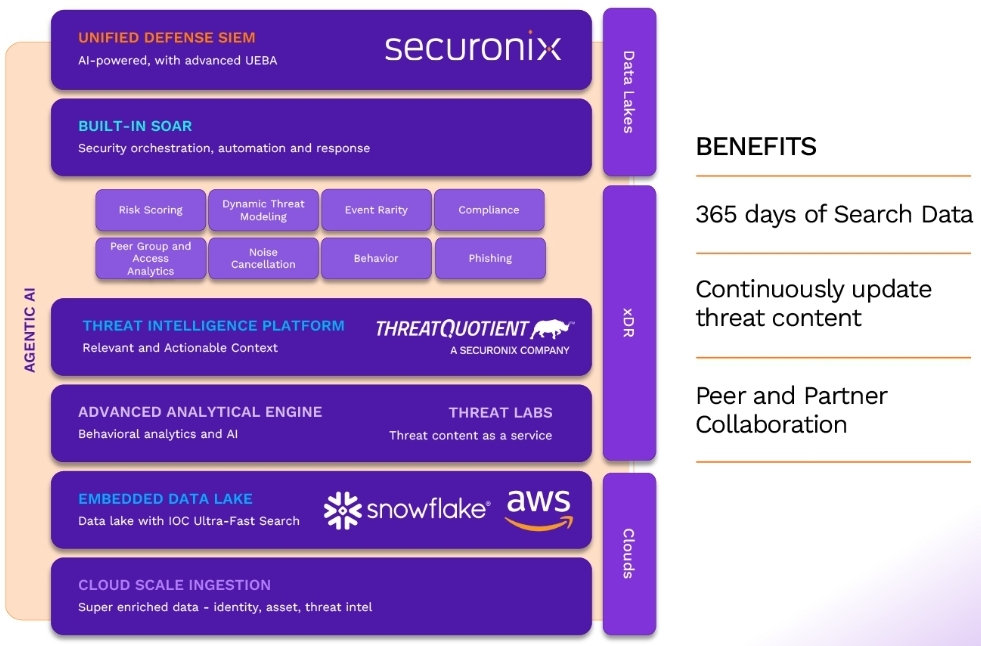
Gartner’s evaluation emphasizes global SaaS architecture availability and platform features like SOAR, UEBA, threat intelligence, self-service analytics, and incident management. These aren’t just technical capabilities. They’re the building blocks of efficient, effective security operations that protect both the business and the experience.
The customer testimonials tell the real story. When HDFC Bank’s CISO says cybersecurity is “integral to customer satisfaction and business performance,” he’s making a direct connection between security operations and experience quality.
At HDFC Bank’s scale, serving over 120 million customers, every security decision has experience implications. Their partnership with Securonix processes over 1.3 million events per second through Data Pipeline Manager. This architecture enables them to maintain security without sacrificing customer experience.
From Reactive to Autonomous: The Agentic AI Transformation
The cybersecurity industry has reached an inflection point. Human-only SOCs cannot keep pace with AI-powered threats. The math simply doesn’t work.
This is where agentic AI changes the game. Not as a replacement for analysts, but as a force multiplier that handles repetitive tasks and frees humans for strategic work.
Agentic AI systems don’t just detect threats. They investigate, correlate, and respond autonomously within defined parameters. They learn from analyst decisions and improve over time. Most importantly, they don’t experience fatigue, frustration, or burnout.
Alberta Health Services demonstrates the impact. Their CISO Richard Henderson reports cutting false positives by over 90% with Securonix. For an organization serving 4.5 to 5 million people across 106 hospitals, 800 clinics, and 150,000 staff, this efficiency gain is transformative.
Consider what 90% fewer false positives means. Analysts spend less time chasing ghosts. They focus on genuine threats. Response times improve. And critically, legitimate user activities stop getting flagged incorrectly.
When a healthcare worker needs urgent access to patient records, the system makes intelligent decisions. It considers context, behavior patterns, and risk factors. It distinguishes between suspicious activity and a doctor working an unusual shift during an emergency.
This is security that enables rather than obstructs.
The ROI Conversation: Speaking the Language of the Boardroom
Boards demand measurable returns on security investments. They want to understand not just what was prevented, but what value was created.
This shift reframes how CISOs approach security operations. The conversation moves from technical metrics to business outcomes. From “we blocked X attacks” to “we enabled $Y in revenue while maintaining zero breaches.”
Securonix CEO Kash Shaikh articulates this clearly: “Boards demand ROI. Analysts face burnout. Legacy SOCs can’t keep up with AI-powered threats.” The solution requires proving that security investments deliver efficiency, innovation, and confidence.
Data Pipeline Manager exemplifies this ROI-focused approach. By intelligently tiering security data, organizations slash storage costs while maintaining full visibility. High-priority logs get real-time analytics. Investigation data retains structure for threat hunting. Compliance logs sit in cost-effective storage.
One Fortune 200 company reduced Splunk ingestion by 430GB daily, saving $400,000 annually. A large healthcare provider cut SIEM costs by over 80% while increasing data retention fourfold. These aren’t just cost savings. They’re budget reallocations toward capabilities that improve both security and experience.
When you can demonstrate that your security platform reduces analyst burnout, cuts false positives by 90%, and decreases data costs by millions, you speak the language executives understand.
The ThreatQuotient Integration: Context at Scale
Security operations suffer from context deficiency. An IP address appears suspicious, but is it actually malicious? An authentication pattern looks odd, but is it a threat or a customer traveling abroad?
Integrating advanced threat intelligence platforms like ThreatQuotient directly into SIEM operations solves this problem. It enriches detections automatically, automates investigation workflows, and gives analysts deeper context for faster, more accurate responses.
This integration matters for experience management because context prevents false positives. When the system knows that an IP address belongs to a legitimate customer using a VPN, it doesn’t block the transaction. When it recognizes normal behavior patterns, it doesn’t lock accounts unnecessarily.
Context enables precision. Precision reduces friction. Reduced friction improves experience.
Building a Modern SOC: People, Process, and Technology
SOC transformation requires rethinking all three foundational elements. Technology alone cannot fix a broken operations model.
People: The talent shortage won’t resolve soon. Organizations must make their SOCs attractive workplaces. This means reducing tedious manual work, providing growth opportunities, and preventing burnout. AI-powered automation handles repetitive tasks. Analysts focus on interesting challenges that develop their skills.
Process: Modern SOCs need clearly defined incident categories, response playbooks, and escalation paths. They require metrics that matter, not vanity numbers. Mean time to detect and respond. False positive rates. Analyst satisfaction scores. Customer impact measurements.
Technology: The platform must scale effortlessly, integrate seamlessly, and adapt continuously. Cloud-native architecture provides flexibility. Built-in analytics deliver insights. Unified interfaces reduce tool sprawl and the “swivel chair problem.”
Alberta Health Services chose the “full spread” of Securonix capabilities: threat detection, investigation, response, behavioral analytics, and security data lake in one integrated platform. This consolidation eliminates silos, speeds investigations, and reduces complexity.
The Employee Experience Dimension
While customer experience gets attention, employee experience in the SOC deserves equal focus. Security analysts face some of the most challenging work conditions in IT.
They monitor networks 24/7. They respond to incidents at 2 AM. Plus, they face consequences when they miss threats. Above all, they endure criticism when security measures inconvenience users.
SOC analyst burnout rates are alarming. Studies show 71% of SOC staff rate workplace stress at 6-9 out of 10. Over half have considered quitting due to pressure. Organizations lose up to 19% of their SOC staff annually.
This turnover is expensive. Recruiting a cybersecurity professional costs approximately $145,000. But the greater cost is institutional knowledge loss and security gaps during understaffing.
Modern SIEM platforms improve analyst experience by eliminating the most frustrating aspects of the job. Automated threat triage ends the endless queue of false alarms. Intelligent correlation surfaces real threats quickly. Integrated workflows eliminate tool-hopping. Collaboration features enable team problem-solving.
When analysts can focus on work that matters, job satisfaction improves. Retention increases. The organization builds deep expertise. Security posture strengthens. And ultimately, both customer and employee experiences benefit.
The Trust Equation: Security, Experience, and Brand Value
Customer trust depends on invisible competence. Customers rarely notice good security. They always notice bad security or security that creates friction.
A data breach costs an average of $4.44 million globally. But the reputational damage often exceeds the immediate financial impact. According to research, 70% of customers would stop doing business with a company after a data breach. Brand recovery takes approximately 11.8 months on average.
On the flip side, companies that demonstrate strong security practices without creating friction build competitive advantage. Security-conscious customers choose providers who protect data effectively. Privacy certifications and transparent security communications build trust.
HDFC Bank’s approach exemplifies this balance. Their CISO emphasizes that “cybersecurity is integral to customer satisfaction and business performance.” They’ve modernized their SOC to maintain security at massive scale while enhancing visibility and streamlining compliance.
This is the modern mandate: protect ruthlessly, but enable seamlessly.
Practical Takeaways for CX and Security Leaders
Align security and experience metrics. Track not just threats blocked, but false positives that impact customers. Measure security friction in customer journeys. Monitor how security controls affect conversion rates and satisfaction scores.
Invest in automation strategically. Deploy AI where it delivers the highest impact: threat triage, alert correlation, routine investigation, and response automation. Free analysts for complex problem-solving and strategic initiatives.
Implement intelligent data management. Not all logs need real-time analytics. Tier your data based on value. Route high-priority security events to hot storage. Send investigation data to warm storage. Archive compliance logs in cold storage. This reduces costs dramatically while maintaining visibility.
Prioritize analyst experience. Your security team’s well-being directly impacts your security posture. Reduce burnout through automation, clear processes, and recognition programs. Develop career paths that encourage retention.
Communicate security as a business enabler. Frame security investments in terms of business outcomes. Calculate risk reduction in dollars. Demonstrate how security enables digital initiatives. Show ROI in language executives understand.
Build integration, not tool sprawl. Each additional security tool increases complexity. Choose platforms that consolidate capabilities. Seek solutions with open architectures that integrate easily with existing investments.
Foster collaboration between security and CX teams. Security professionals understand threats. CX professionals understand customer journeys. Together, they can design security that protects without obstructing.
The Path Forward
The recognition of platforms like Securonix as Leaders in the SIEM space signals an industry evolution. The market is moving beyond feature checklists toward solutions that solve real operational challenges.
Organizations that modernize their security operations gain multiple advantages. They detect threats faster. They respond more effectively. Plus, they reduce costs. Above all, they improve analyst retention. And critically, they protect customer and employee experiences.
This isn’t about security versus experience. It’s about recognizing that in a digital world, security is experience. Every fraud prevention decision affects a customer. Every access control impacts an employee. Above all, every alert consumes analyst capacity that could go toward genuine threats.
The future belongs to organizations that view security operations as strategic enablers of experience, not necessary evils that create friction. Those who embrace AI-powered automation, intelligent data management, and unified platforms will outperform competitors on security, efficiency, and experience simultaneously.
Six consecutive years as a Gartner Leader isn’t just about technology. It’s about understanding that the best security is invisible to legitimate users, empowering to security teams, and measurable to executives. That’s the standard modern organizations must meet.