Adopt Zero Trust Security Before Your Next Security Breach Comes from That Coffee Shop Wi-Fi
Picture this: Your employee Sarah opens her laptop at a bustling downtown café. She logs into your corporate network seamlessly. However, her device hasn’t updated security patches in weeks. Meanwhile, the café’s Wi-Fi broadcasts to dozens of unknown devices nearby. This is definitely going to puncture your corporate network security unless it has a strong zero trust security deployed.
This scenario plays out thousands of times daily across organizations worldwide. Additionally, it represents exactly why traditional security approaches fail modern workplaces.
The Reality Check: Your Office Isn’t Your Castle Anymore
Today’s workforce operates from everywhere except traditional office spaces. Consequently, employees connect from homes, airports, and co-working spaces using various devices. Furthermore, this shift brings unprecedented flexibility alongside significant security challenges.
Previously, organizations relied on perimeter-based security models. These systems assumed everything inside the network was trustworthy. However, this approach crumbles when your “perimeter” includes every coffee shop with Wi-Fi.
Moreover, the device landscape has become increasingly complex. Personal smartphones access corporate email. Tablets download sensitive documents. Home computers join video conferences with confidential information. Each connection point creates potential vulnerability.
Enter Hexnode’s Strategic Response
Recognizing these evolving challenges, Hexnode announces expanded Zero Trust capabilities. The platform now integrates advanced compliance controls with conditional access frameworks. Additionally, these enhancements address the fundamental question: How do you maintain security when your network extends everywhere?
The announcement, released on July 15th, 2025, represents a comprehensive approach to modern security challenges. Furthermore, it signals Hexnode’s commitment to evolving alongside changing workplace dynamics.
Breaking Down the Compliance Challenge
Traditional compliance checking happens once during initial login. Subsequently, devices maintain access regardless of changing security conditions. This creates dangerous gaps where compromised devices continue accessing sensitive data.
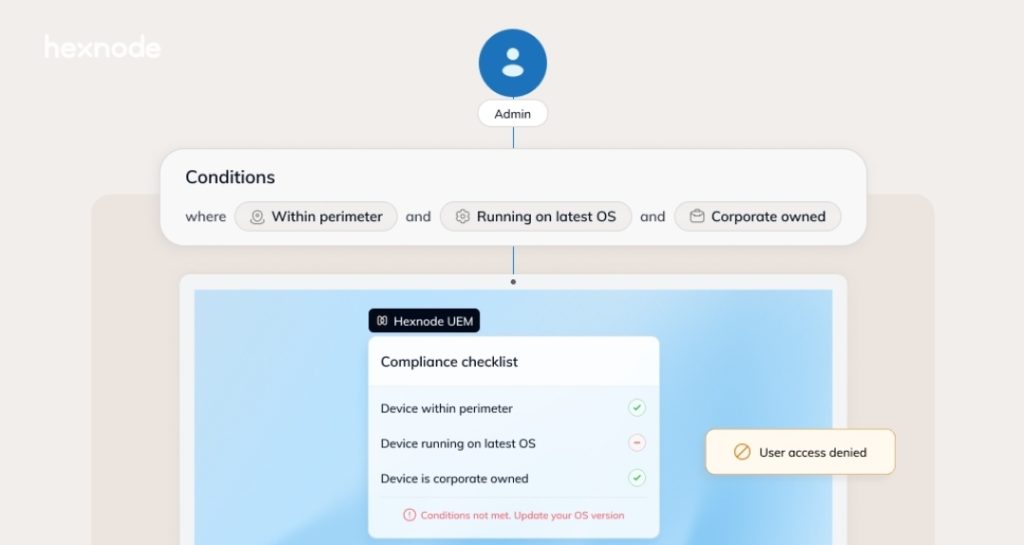
Hexnode’s enhanced framework changes this dynamic completely. Instead of one-time verification, the system monitors device compliance continuously. Consequently, any deviation from security standards triggers immediate response protocols.
The platform now supports granular compliance policies across iOS, Android, Windows, and macOS platforms. These policies monitor device inactivity, enforce geofencing restrictions, and verify application compliance. Additionally, they track real-time metrics including battery levels, encryption status, and network connectivity.
Advanced Compliance: Beyond Basic Requirements
Basic compliance checking addresses fundamental security requirements. However, modern threats require sophisticated countermeasures. Therefore, Hexnode introduces Advanced Compliance Policies with customizable multi-condition rules.
These policies enable IT administrators to create complex compliance scenarios. For example, they can enforce different security levels based on device ownership models. Corporate-owned devices might require stricter controls than personal devices accessing limited resources.
Furthermore, the system evaluates live network status and device health metrics. Battery levels below certain thresholds might trigger security warnings. Unencrypted devices automatically lose access to sensitive applications. Network anomalies prompt additional authentication requirements.
This granular approach ensures every device meets organizational standards continuously. Additionally, it provides IT teams with unprecedented visibility into their security posture.
The Microsoft Intune Integration: A Strategic Partnership
While continuous compliance secures devices after access, controlling initial entry remains crucial. Previously, organizations granted access based primarily on user credentials. This approach ignored device security status entirely.
Hexnode’s integration with Microsoft Intune’s third-party compliance program addresses this limitation. Now, every login attempt undergoes comprehensive evaluation against predefined security conditions. Even valid credentials won’t guarantee access from non-compliant devices.
This partnership leverages Microsoft’s conditional access capabilities alongside Hexnode’s device management expertise. Consequently, organizations benefit from both platforms’ strengths without managing separate systems.
The integration evaluates multiple factors before granting access. Location-based triggers identify unusual login patterns. Device compliance scores determine access levels. Network conditions influence authentication requirements. Together, these factors create a comprehensive security assessment.
Risk-Based Authentication: The New Standard
Traditional authentication relied heavily on “something you know” – passwords and PINs. However, modern threats exploit weak passwords and compromised credentials regularly. Therefore, effective security requires evaluating “something you have” and “something you are.”
Hexnode’s conditional access framework introduces risk-based authentication protocols. The system analyzes user behavior patterns, device characteristics, and environmental factors. Subsequently, it determines appropriate authentication requirements for each access attempt.
Low-risk scenarios might require standard login credentials. Medium-risk situations could trigger multi-factor authentication. High-risk attempts might block access entirely pending administrative review.
This dynamic approach adapts to changing threat landscapes continuously. Additionally, it reduces friction for legitimate users while increasing barriers for potential attackers.
Looking Forward: Okta Integration and Beyond
Hexnode’s roadmap includes extending Zero Trust capabilities to Okta users through Okta Device Trust. This expansion will strengthen security across diverse identity platforms. Furthermore, it demonstrates Hexnode’s commitment to comprehensive identity management solutions.
The Okta integration will provide similar conditional access capabilities for organizations using Okta’s identity platform. Consequently, businesses can maintain consistent security policies regardless of their chosen identity provider.
The Business Impact: Security Meets Productivity
These enhancements address a critical business challenge: maintaining security without hindering productivity. Traditional security measures often created friction that reduced employee efficiency. Conversely, overly permissive policies exposed organizations to significant risks.
Hexnode’s approach balances these competing priorities effectively. Compliant devices experience seamless access to required resources. Non-compliant devices face appropriate restrictions until they meet security standards. This balance maintains productivity while enforcing necessary security measures.
Moreover, the unified console simplifies management for IT administrators. Previously, compliance monitoring required multiple tools and dashboards. Now, administrators can manage comprehensive security policies from a single interface.
The Technical Foundation: Unified Endpoint Management
Hexnode’s enhanced capabilities build upon its established Unified Endpoint Management (UEM) platform. This foundation supports comprehensive device management across major platforms including Android, Windows, Linux, iOS, macOS, ChromeOS, Fire OS, vision OS, and tvOS.
The platform’s cloud-based architecture ensures scalability and reliability. Organizations can manage thousands of devices without infrastructure concerns. Additionally, regular updates deliver new features and security enhancements automatically.
Conclusion: The Future of Enterprise Security
Hexnode’s expanded Zero Trust capabilities represent more than feature additions. They signal a fundamental shift toward continuous security verification. In an era where threats evolve rapidly, static security measures prove inadequate.
The combination of advanced compliance controls and conditional access creates a robust security framework. This framework adapts to changing conditions while maintaining user productivity. Furthermore, it provides organizations with the tools needed to secure modern, distributed workforces.
As workplace dynamics continue evolving, security strategies must evolve accordingly. Hexnode’s latest enhancements position organizations to meet these challenges head-on. By implementing continuous verification and risk-based authentication, businesses can maintain security without sacrificing flexibility.
The future belongs to organizations that embrace adaptive security models. Hexnode’s enhanced platform provides the foundation for this transformation.