CyberArk and Microsoft Defender for Identity Integration: Elevating Cyber Threat Management
The integration of CyberArk Privileged Access Manager (PAM) with Microsoft Defender for Identity has revolutionized cyber threat management. Announced on January 16, 2025, this partnership enables organizations to achieve a unified and comprehensive view of their identity security landscape. This collaboration enhances the speed and effectiveness of threat identification and containment, ultimately strengthening cyber resilience.
Understanding Microsoft Defender for Identity
Microsoft Defender for Identity is a cloud-based identity security solution specifically designed to protect on-premises identities. It plays a critical role in managing identity risk and defending against advanced threats. Fully integrated with Microsoft Defender Extended Detection and Response (XDR), this solution uses signals from hybrid identity environments and diverse workloads. Consequently, Security Operations (SecOps) teams gain enhanced capabilities to identify, detect, and investigate sophisticated cyber threats.
By leveraging signals across hybrid infrastructures, Defender for Identity offers a detailed analysis of vulnerabilities. It empowers organizations to mitigate risks effectively, making it a vital tool in modern cybersecurity strategies.
CyberArk Privileged Access Manager: A Robust Solution
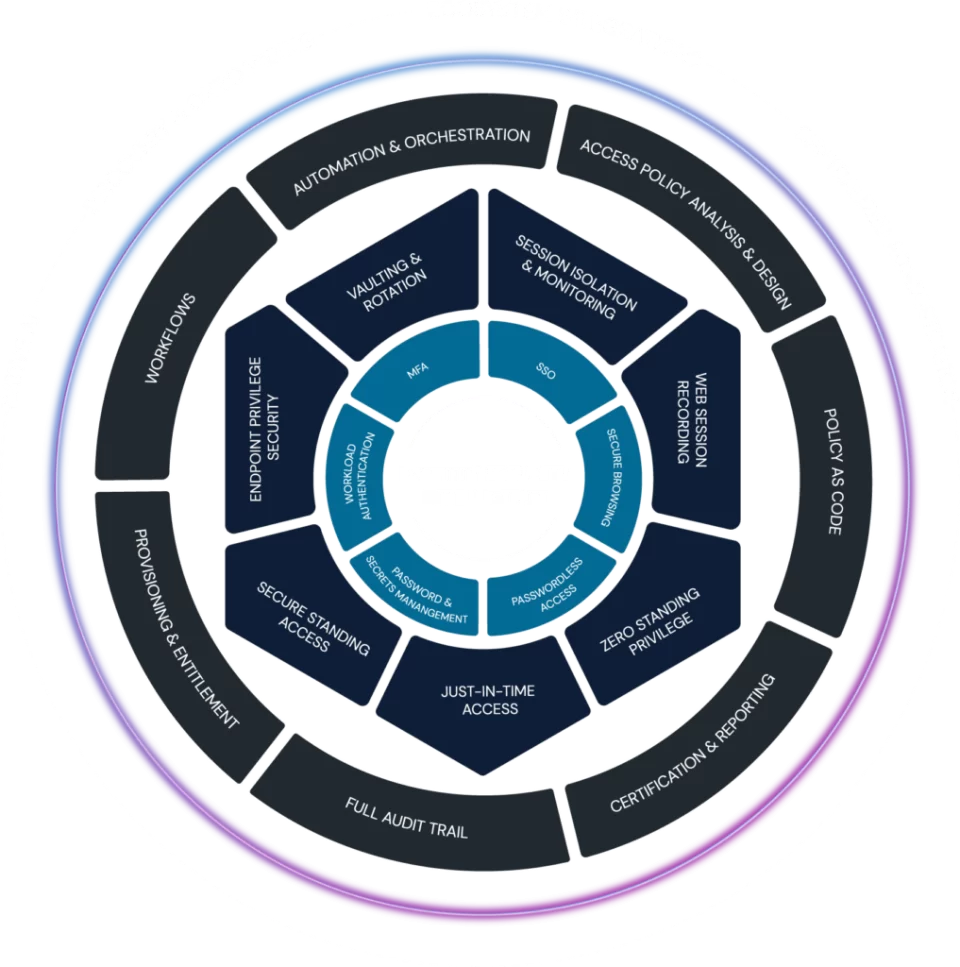
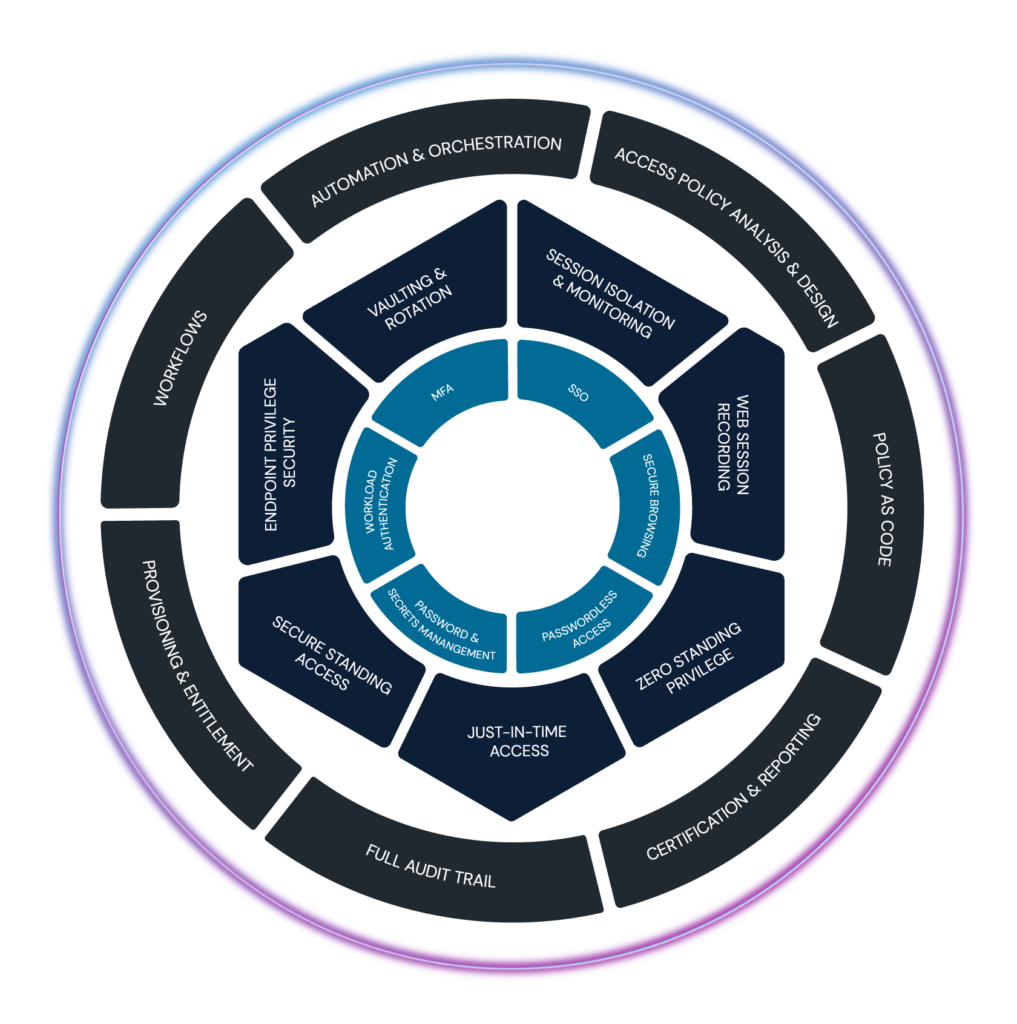
CyberArk Privileged Access Manager, a pivotal component of the CyberArk Identity Security Platform, offers unparalleled control over privileged access. It provides comprehensive tools to discover, secure, and monitor privileged accounts across IT and cloud operations. For organizations operating in hybrid and multi-cloud environments, PAM delivers best-in-class solutions that simplify migration, scaling, and application management.
The integration of CyberArk Privileged Access Manager with Microsoft Defender for Identity enhances privileged access control and monitoring capabilities. This collaboration provides organizations with streamlined workflows, ensuring seamless operations while addressing cybersecurity challenges.
Key Benefits of the Integration
This integration between CyberArk PAM and Microsoft Defender for Identity offers several significant advantages, ensuring organizations stay ahead of cyber threats:
- Enhanced Threat Detection
By connecting data from diverse systems, the integration allows for deeper investigative capabilities. Security teams can quickly identify attack paths and threats, reducing the time required for response and remediation. - Streamlined Workflows
The integration simplifies privileged access workflows, enabling seamless operations for Security Operations Center (SOC) and identity teams. This streamlining ensures higher efficiency and effectiveness in managing cyber risks. - Improved Cyber Resilience
Organizations benefit from robust protection against identity-centric attacks. The collaboration between CyberArk and Microsoft Defender for Identity ensures comprehensive defense mechanisms, safeguarding critical assets. - Optimized Investment
Leveraging existing infrastructure, the integration maximizes organizations’ investments in cybersecurity solutions. It provides a cost-effective way to enhance identity security without requiring significant additional resources. - Comprehensive Monitoring
With improved privileged access monitoring, organizations can proactively address vulnerabilities. This comprehensive approach ensures a higher level of security across all identity environments.
A Strategic Partnership
Clarence Hinton, Chief Strategy Officer at CyberArk, emphasized the importance of this collaboration. He stated, “Through the CyberArk C³ Alliance’s diverse ecosystem of partners, we continue to provide unparalleled protection for shared customers against identity-centric attacks. CyberArk’s privileged access management integration with Defender for Identity allows organizations to maximize their existing investment and simplify their efforts to protect identities across their on-premises and multi-cloud environments.”
This partnership highlights CyberArk’s commitment to innovation and customer-centric solutions. By addressing complex cybersecurity challenges, it ensures that organizations can navigate an ever-evolving threat landscape with confidence.
Enhancing Security Operations
Security Operations Center (SOC) teams play a pivotal role in safeguarding organizations from cyber threats. The integration of CyberArk PAM and Microsoft Defender for Identity empowers SOC teams with advanced tools for threat detection and management. These tools facilitate quicker threat-hunting efforts, enabling teams to identify and neutralize threats effectively.
Additionally, the integration supports SOC teams in identifying attack paths with greater precision. This capability is crucial for implementing targeted remediation strategies, minimizing the impact of potential breaches.
Empowering Identity Teams
Identity teams also benefit significantly from this integration. The seamless connection of data across systems enables better monitoring of privileged access. This capability ensures that identity teams can proactively address vulnerabilities, preventing unauthorized access and reducing the risk of data breaches.
Moreover, the integration simplifies identity workflows, allowing teams to focus on strategic initiatives. By streamlining operational processes, it enhances overall productivity and efficiency.
The Role of Artificial Intelligence and Machine Learning
The integration leverages cutting-edge technologies such as Artificial Intelligence (AI) and Machine Learning (ML). These technologies play a crucial role in enhancing threat detection capabilities. By analyzing patterns and behaviors, AI and ML enable the system to identify anomalies and potential threats with high accuracy.
This advanced approach ensures that organizations can stay ahead of emerging threats. It also supports continuous improvement in cybersecurity measures, adapting to the dynamic nature of cyber risks.
A Future-Ready Solution
As cyber threats continue to evolve, organizations must adopt future-ready solutions. The integration of CyberArk PAM and Microsoft Defender for Identity represents a significant step in this direction. By providing robust identity security solutions, it ensures that organizations can protect their critical assets and maintain operational continuity.
About CyberArk
CyberArk (NASDAQ: CYBR) is a global leader in identity security, focusing on intelligent privilege controls. The company offers the most comprehensive security solutions for any identity—human or machine—across various environments. Trusted by the world’s leading organizations, CyberArk is committed to securing critical assets and enabling digital transformation.
Conclusion
The integration of CyberArk Privileged Access Manager with Microsoft Defender for Identity sets new standards in identity security. By providing enhanced threat detection, streamlined workflows, and comprehensive monitoring, it empowers organizations to navigate the complexities of modern cybersecurity. This partnership underscores the importance of innovation and collaboration in addressing identity-centric attacks, ensuring a secure future for businesses worldwide.
Key CX Takeaways:
- Enhanced Threat Detection: Organizations benefit from advanced tools that enable quicker identification and resolution of cyber threats.
- Streamlined Workflows: SOC and identity teams can work more efficiently with seamless privileged access workflows and integration.
- Improved Resilience: Comprehensive monitoring and AI-driven insights bolster defenses against identity-centric attacks in hybrid environments.
- Optimized Investments: Businesses can maximize the value of their existing security infrastructure while gaining cutting-edge identity protection.
- Future-Ready Security: The integration sets a new standard in cybersecurity, ensuring readiness against evolving threats.