When Trust Becomes Your Biggest Vulnerability: How Social Engineering Is Reshaping Customer Security in 2025
Your customers trust you. Furthermore, that trust drives every interaction, every transaction, and every relationship your business builds. However, what happens when cybercriminals weaponize that very trust against you? Additionally, the 2025 Unit 42 Global Incident Response Report reveals a sobering reality: social engineering has evolved from simple email scams into sophisticated, AI-powered attacks that bypass traditional security measures by targeting human behavior.
The New Reality of Trust-Based Attacks
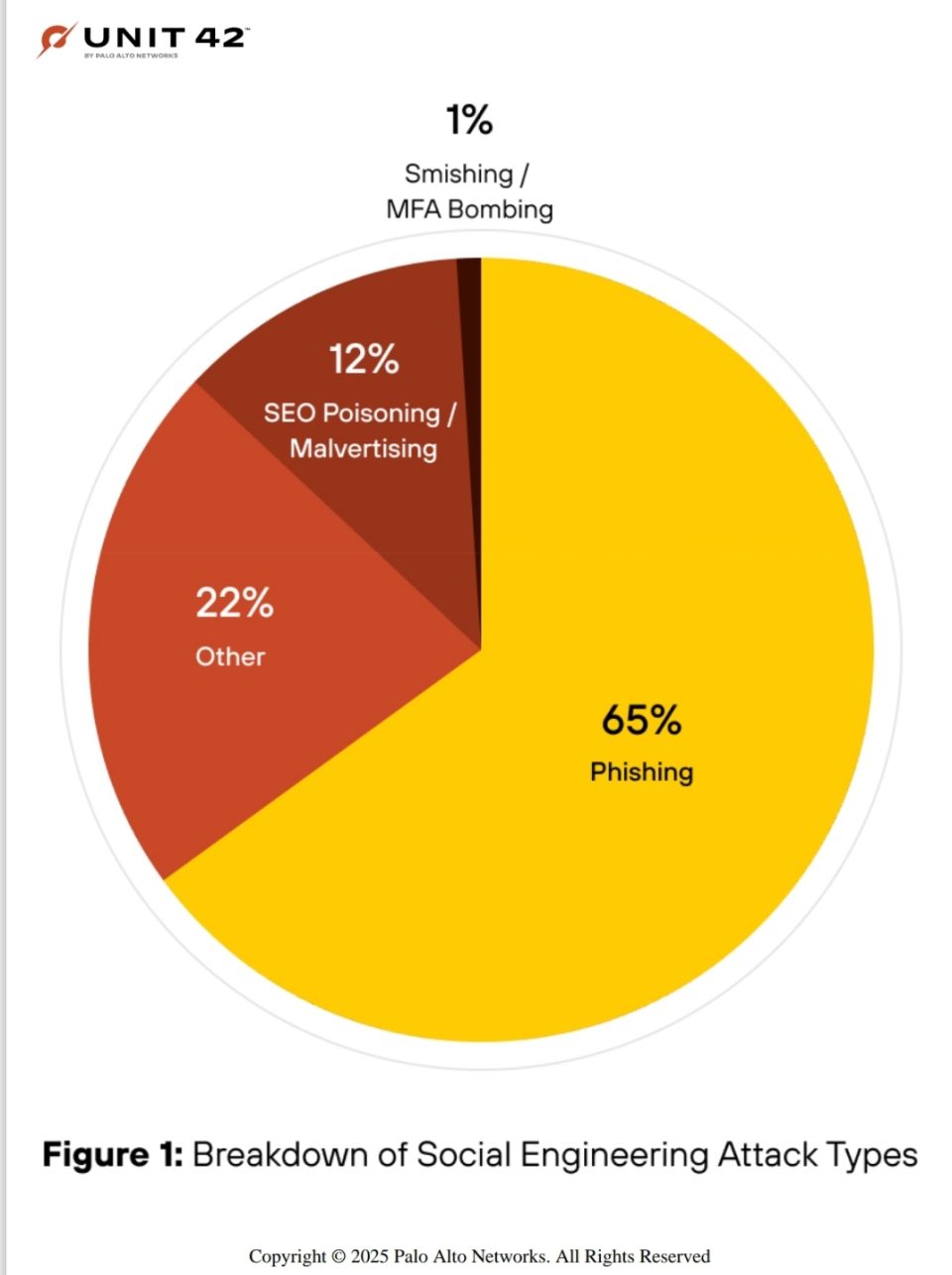
Social engineering attacks now account for 36% of all security incidents, making them the single most effective entry point for cybercriminals. Moreover, these aren’t the crude phishing emails of the past. Today’s attacks combine psychological manipulation with cutting-edge technology to create nearly undetectable deceptions.
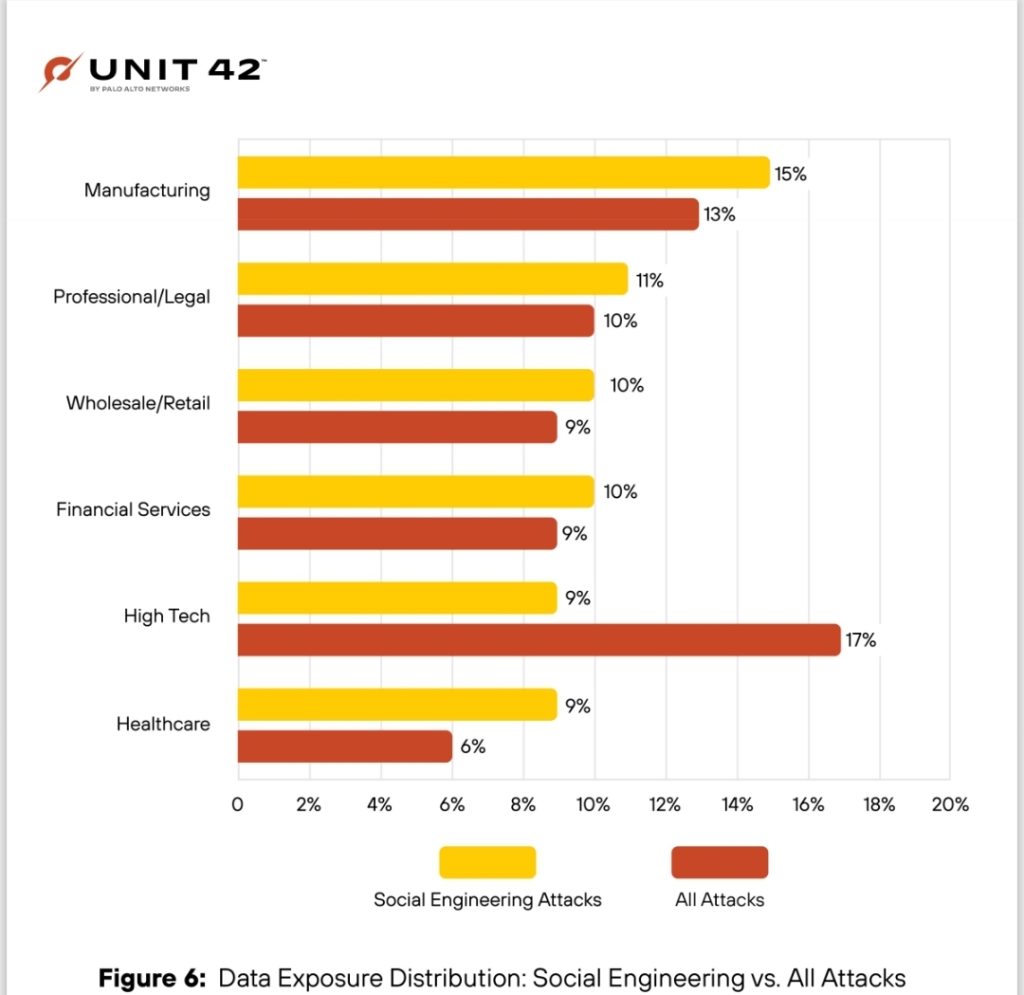
Consider this: 66% of social engineering attacks target privileged accounts, while 60% lead to data exposure. Consequently, when these attacks succeed, they don’t just breach your systems—they shatter the trust your customers place in your organization. Furthermore, with 98% of cyberattacks leveraging social engineering, particularly phishing, businesses can no longer treat this as a secondary concern.
High-Touch Attacks: When Criminals Call Your Help Desk
Perhaps most concerning is the rise of “high-touch” attacks, where cybercriminals impersonate employees and manipulate your own staff to gain access. Additionally, groups like Muddled Libra demonstrate how effective these tactics can be, progressing from initial access to domain administrator rights in under 40 minutes without deploying any malware.
These attackers don’t break systems—they understand them. Moreover, they study your organizational structure, research your employees on LinkedIn, and craft convincing personas that fool even trained security professionals. In one documented case, attackers staged and exfiltrated over 350 GB of data simply by calling the help desk and convincing staff to reset multi-factor authentication credentials.
The AI Revolution in Social Engineering
Artificial intelligence has fundamentally transformed the social engineering landscape. Consequently, cybercriminals now use three distinct layers of AI-enabled tooling:
Automation streamlines traditional attack methods, while Generative AI creates highly personalized, human-like content across multiple channels. Meanwhile, Agentic AI executes complex, multi-step attacks with minimal human oversight, including the creation of synthetic identities for insider campaigns.
Voice cloning technology exemplifies this evolution. With just three seconds of audio, attackers can create convincing voice replicas that pass both automated systems and human verification. Recent threat intelligence shows that deepfake-enabled vishing surged by over 1,600% in the first quarter of 2025. Therefore, what was once the domain of science fiction has become a daily reality for security teams worldwide.
The Scale of ClickFix Campaigns
Simultaneously, “ClickFix” campaigns represent the scalable side of modern social engineering. These attacks use fake browser alerts, fraudulent update prompts, and SEO poisoning to trick users into initiating their own compromise. Between May 2024 and May 2025, ClickFix was the initial access vector in at least eight confirmed incident response cases.
The technique succeeds because it mimics trusted workflows. Moreover, users encounter what appears to be a legitimate Microsoft update notification or Google CAPTCHA verification. Instead, clicking these prompts downloads malware that harvests credentials and establishes persistent access. Because users initiate the action themselves, these attacks often bypass traditional perimeter defenses.
The Customer Trust Crisis
When social engineering attacks succeed, the impact extends far beyond immediate financial losses. Research shows that 65% of consumers lose trust in a business after a data breach, with many vowing never to return. Additionally, 40% of customers abandon companies after security incidents.
The financial implications are staggering. Business Email Compromise (BEC) alone resulted in $2.7 billion in losses in 2022. Furthermore, the average cost of a social engineering-related breach exceeds $4 million, with recovery often taking months. For small businesses, these costs can range from $120,000 to $1.24 million, potentially threatening their very survival.
Beyond Financial Loss: The Reputation Cascade
However, the damage extends beyond immediate financial impact. Social engineering attacks create a cascade effect that undermines customer relationships:
Immediate Impact: Direct financial losses, recovery costs, and operational disruption
Short-term Consequences: Negative publicity, customer churn, and increased insurance premiums
Long-term Effects: Damaged brand reputation, difficulty acquiring new customers, and reduced market value
Studies indicate that businesses lose approximately 36% of customers after a security incident, creating long-term revenue impacts that dwarf initial breach costs.
The Detection Gap: Why Traditional Security Falls Short
Despite massive investments in cybersecurity technology, organizations continue to fall victim to social engineering attacks. The Unit 42 report identifies several critical gaps:
Alert Fatigue: Security teams routinely miss or dismiss critical warnings due to information overload
Insufficient Coverage: Many organizations lack Identity Threat Detection and Response (ITDR) or User and Entity Behavior Analytics (UEBA) capabilities
Weak Controls: Over-permissioned accounts and inadequate multi-factor authentication create opportunities for escalation
These gaps exist because traditional security models focus on technical vulnerabilities rather than human behavior. Consequently, attackers exploit the spaces between people, processes, and platforms where trust operates without verification.
Building Resilience: A Customer-Centric Security Approach
Protecting against social engineering requires a fundamental shift in security strategy. Rather than treating it as a training problem, organizations must recognize social engineering as a systemic vulnerability requiring technical controls and identity-focused defenses.
Identity-First Security Architecture
Modern ITDR solutions address the gap between traditional Identity and Access Management (IAM) and actual threat detection. These systems monitor authentication events, analyze behavioral anomalies, and detect privilege escalations before they occur. Moreover, they integrate seamlessly with existing security architectures, correlating identity signals across cloud, on-premises, and hybrid environments.
Key capabilities include:
- Continuous Monitoring: Real-time analysis of user behavior patterns
- Contextual Intelligence: Correlation of authentication logs, device signals, and user behaviors
- Automated Response: Immediate account isolation, access revocation, and step-up authentication
Zero Trust Implementation
Zero Trust architecture extends beyond network perimeters to encompass user verification at every interaction point. This approach assumes breach and continuously validates both identity and behavior throughout user sessions. Furthermore, conditional access policies assess device trust, location, and login behavior before granting system access.
Essential components include:
- Least-Privilege Access: Minimal permissions granted for specific tasks
- Just-in-Time Provisioning: Temporary elevated access for privileged operations
- Network Segmentation: Limited lateral movement capabilities
- Behavioral Analytics: Continuous monitoring for anomalous activity patterns
Advanced Detection Capabilities
Organizations must deploy detection systems specifically designed for social engineering attacks. This includes Advanced DNS Security and URL filtering to block malicious infrastructure, while behavioral baselines help identify unusual activity patterns that indicate compromise.
Additionally, correlation engines analyze signals across identity, endpoint, network, and SaaS activity to expose escalation attempts early. These systems integrate with Security Operations Center (SOC) workflows to accelerate response times and reduce alert fatigue.
The Human Factor: Training That Actually Works
While technology provides the foundation, human awareness remains crucial. However, effective training has evolved beyond annual compliance sessions to continuous, engaging programs that simulate real-world attack scenarios.
Modern training approaches include:
- Simulated Phishing Exercises: Regular testing with current attack techniques
- Gamified Learning: Interactive modules that engage employees
- Role-Specific Training: Targeted education for high-risk positions like IT support and finance
- Threat Intelligence Integration: Real-time updates based on emerging attack patterns
Research demonstrates that regular social engineering training can stop most attacks, but only when combined with robust technical controls and clear incident response procedures.
Looking Forward: Preparing for Tomorrow’s Threats
The social engineering threat landscape will continue evolving as AI technology advances. Organizations must prepare for increasingly sophisticated attacks that blur the lines between real and synthetic communications.
Future considerations include:
- Quantum-Resistant Cryptography: Protection against future computational capabilities
- Passwordless Authentication: Elimination of credential-based attack vectors
- AI-Powered Defense: Machine learning systems that evolve with attack techniques
- Identity Fabric: Comprehensive identity governance across all digital touchpoints
Regulatory and Compliance Evolution
Regulatory frameworks are adapting to address social engineering risks. Organizations must prepare for enhanced disclosure requirements, stricter liability standards, and increased penalties for inadequate security practices. Moreover, customer protection regulations will likely expand to cover AI-generated deceptions and synthetic media attacks.
Building Customer Trust Through Security Excellence
Ultimately, defending against social engineering isn’t just about preventing attacks—it’s about demonstrating to customers that their trust is valued and protected. Organizations that proactively address these threats create competitive advantages through enhanced customer confidence and reduced risk exposure.
Effective social engineering defense requires:
- Executive Commitment: Leadership recognition of social engineering as a business-critical risk
- Cross-Functional Collaboration: Integration of security, IT, and business teams
- Continuous Improvement: Regular assessment and enhancement of security measures
- Transparency: Clear communication with customers about security practices and incident response
The threat landscape has fundamentally changed. Social engineering attacks now combine psychological manipulation with advanced technology to create unprecedented risks to customer trust and business continuity. However, organizations that recognize this reality and implement comprehensive, identity-focused defenses can transform their security posture from liability to competitive advantage.
Success requires moving beyond traditional approaches to embrace identity-centric security, continuous monitoring, and human-focused training programs. Most importantly, it demands recognition that in today’s threat environment, protecting customer trust isn’t just a security imperative—it’s a business survival strategy.
The choice is clear: adapt to the new reality of trust-based attacks, or risk becoming another statistic in the growing catalog of social engineering victims. Your customers’ trust depends on the decision you make today.