The AI-Driven Evolution: How Proactive Cybersecurity is Transforming India’s Digital Defense Strategy
The cybersecurity landscape is witnessing a fundamental transformation across India. Organizations are increasingly recognizing that traditional reactive security approaches are insufficient against sophisticated modern threats. This shift toward proactive, AI-powered defense strategies represents more than a technological upgrade—it marks a strategic imperative for businesses operating in our rapidly digitalizing economy.
From Reactive Response to Predictive Defense
The paradigm shift from reactive to proactive cybersecurity represents a profound change in organizational mindset. While reactive approaches wait for threats to materialize before responding, proactive security leverages artificial intelligence to anticipate, predict, and prevent attacks before they occur.
Nevertheless, this transformation isn’t merely about deploying better detection tools. Furthermore, it requires organizations to fundamentally reimagine their security posture, moving from alert-driven firefighting to intelligence-led threat hunting. Additionally, AI-powered systems analyze vast datasets to identify patterns and anomalies that human teams might miss.
Moreover, proactive security strategies incorporate continuous monitoring and real-time risk assessment. Consequently, organizations can address vulnerabilities before they become exploitable weaknesses. Similarly, predictive analytics enable security teams to allocate resources more effectively, focusing on the highest-risk scenarios.
The Intelligence Revolution: AI-Powered Threat Detection
Artificial intelligence is revolutionizing cybersecurity operations across multiple dimensions. Traditional signature-based detection systems struggle against polymorphic malware and zero-day exploits, while AI systems excel at behavioral analysis and anomaly detection.
Furthermore, machine learning algorithms continuously evolve their understanding of normal network behavior. Consequently, they can identify subtle deviations that indicate potential threats. Additionally, AI systems process millions of security events simultaneously, correlating data across endpoints, networks, and cloud environments.
Notably, organizations implementing AI-driven cybersecurity report significant improvements in threat detection rates. According to IBM research, companies achieve 98% threat detection rates while reducing incident response times by 70%. Similarly, AI-powered systems demonstrate particular effectiveness in identifying advanced persistent threats and insider attacks.
However, the true power of AI lies in its predictive capabilities. Rather than simply detecting existing threats, advanced systems can forecast attack scenarios based on historical patterns and current threat intelligence. This enables security teams to implement countermeasures before attacks materialize.
Extended Detection and Response: Breaking Down Security Silos
Extended Detection and Response (XDR) frameworks represent the next evolution in cybersecurity architecture. Unlike traditional point solutions that operate in isolation, XDR platforms provide unified visibility across an organization’s entire digital ecosystem.
Moreover, XDR solutions correlate security telemetry from multiple sources including endpoints, networks, cloud applications, and identity systems. Consequently, security analysts gain comprehensive visibility into attack chains that might otherwise remain hidden across disparate security tools.
Additionally, XDR platforms incorporate automated response capabilities that dramatically reduce containment times. When threats are detected, systems can automatically isolate compromised devices, block malicious network traffic, and disable compromised user accounts. These automated responses occur within seconds rather than hours or days required for manual intervention.
Furthermore, XDR frameworks excel at incident prioritization, using AI-driven risk scoring to highlight the most critical threats. This capability is essential given that enterprise security teams often face thousands of alerts daily. By focusing analyst attention on high-priority incidents, organizations can maximize their security team effectiveness.
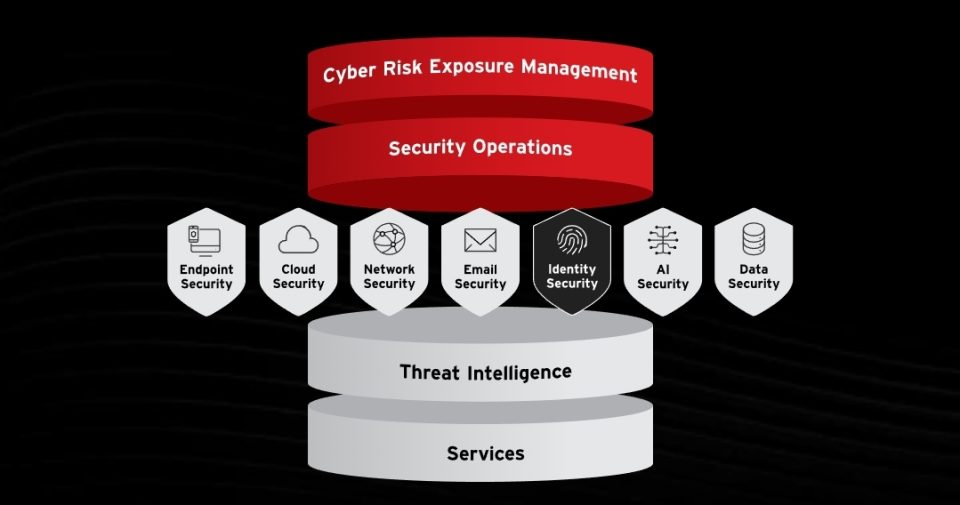
Cyber Risk Exposure Management: Business-Aligned Security
Traditional cybersecurity approaches often treat all assets equally, regardless of their business criticality. However, modern Cyber Risk Exposure Management (CREM) frameworks take a business-aligned approach to risk assessment and mitigation.
Specifically, CREM solutions provide continuous visibility into an organization’s attack surface, identifying all digital assets and their associated risk levels. This comprehensive asset inventory enables security teams to prioritize protection efforts based on business impact rather than technical severity alone.
Moreover, CREM platforms integrate threat intelligence with asset criticality assessments. Consequently, organizations can focus their security investments on protecting their most valuable assets against the most likely threats. This approach maximizes security ROI while reducing overall risk exposure.
Additionally, CREM solutions enable proactive vulnerability management by identifying potential attack paths before they’re exploited. Security teams can simulate various attack scenarios and implement appropriate countermeasures. This capability transforms vulnerability management from a reactive patch cycle to a proactive risk mitigation process.
The Agentic AI Revolution: Autonomous Security Operations
Agentic AI represents the cutting edge of cybersecurity automation, introducing autonomous systems capable of complex decision-making and multi-step response orchestration. Unlike traditional automation tools that follow predefined scripts, agentic AI systems can adapt their behavior based on contextual understanding and evolving threat landscapes.
Furthermore, agentic AI systems excel at autonomous threat hunting, continuously searching for indicators of compromise across enterprise environments. These systems don’t simply wait for alerts; instead, they proactively investigate suspicious activities and correlate events across multiple data sources.
Additionally, agentic AI enables sophisticated attack simulation and red team testing. These systems can autonomously conduct penetration testing, identifying vulnerabilities and recommending remediation strategies. This capability ensures continuous security assessment rather than periodic vulnerability scans.
However, the most significant advantage of agentic AI lies in its collaborative intelligence approach. Multiple AI agents can work together, sharing information and coordinating responses across different security domains. This collaborative model mirrors human security team workflows while operating at machine speed and scale.
Trend Cybertron: The Industry’s First Cybersecurity LLM
Trend Micro’s introduction of Cybertron marks a watershed moment in cybersecurity AI development. As the industry’s first specialized cybersecurity large language model, Cybertron combines 35 years of threat intelligence with advanced AI reasoning capabilities.
Moreover, Cybertron integrates seamlessly with Trend Vision One platform, leveraging all core security technologies including threat data, analytics engines, and response automation. This integration enables comprehensive protection across an organization’s entire digital estate.
Additionally, Cybertron demonstrates remarkable effectiveness in real-world deployments. Customer reports indicate up to 99% faster remediation times when using Cybertron-powered security operations. These improvements stem from the system’s ability to automatically prioritize threats, recommend response actions, and coordinate remediation efforts.
Furthermore, Cybertron’s agentic AI capabilities enable autonomous security operations at unprecedented scale. The system can simultaneously monitor millions of security events, correlate threat intelligence, and execute response playbooks without human intervention. This automation allows human security analysts to focus on strategic initiatives rather than routine operational tasks.
Bengaluru: India’s Cybersecurity Innovation Hub
Bengaluru continues to solidify its position as India’s premier cybersecurity destination. The city hosts numerous global cybersecurity companies alongside innovative startups developing next-generation security solutions.
Moreover, Bengaluru’s cybersecurity ecosystem benefits from strong government support and substantial private sector investment. The Karnataka government actively promotes cybersecurity initiatives through policy frameworks and industry partnerships. This supportive environment accelerates innovation and talent development across the region.
Additionally, the city’s educational institutions produce skilled cybersecurity professionals who drive industry growth. Universities offer specialized cybersecurity programs while research institutions advance the state of security science. This talent pipeline ensures Bengaluru maintains its competitive advantage in cybersecurity innovation.
Furthermore, Bengaluru serves as a testing ground for advanced cybersecurity technologies. Companies like Trend Micro use their Bengaluru presence to develop and validate solutions for global markets. This local innovation has global impact, positioning India as a cybersecurity technology leader.
The Critical Threat Landscape: Understanding India’s Cybersecurity Challenges
India faces significant cybersecurity challenges that underscore the urgent need for proactive defense strategies. According to recent threat intelligence reports, India ranks third globally and second in Asia for malware detections, contributing 4.74% of global malicious activity with 19.3 million threats identified.
Moreover, the threat landscape continues to evolve with increasing sophistication. Behavior-based malware detections have increased from 12.5% to 14.5%, indicating that attackers are developing more advanced evasion techniques. This evolution requires corresponding advances in defensive capabilities.
Additionally, critical infrastructure sectors including banking, financial services, and government agencies face persistent targeting by cyber adversaries. The concentration of attacks on these sectors highlights the need for sector-specific security strategies and enhanced information sharing.
Furthermore, the emergence of AI-powered attack tools is accelerating threat evolution. Cybercriminals are leveraging automation and machine learning to scale their operations and reduce attack timelines from weeks to hours. This acceleration requires equally advanced defensive responses.
Market Growth and Investment Trends
India’s cybersecurity market demonstrates robust growth prospects, reflecting the increasing importance of digital security. The market is expected to grow from $1.97 billion in 2020 to $3.05 billion by 2025, representing a compound annual growth rate of 15.6%.
Moreover, this growth is driven by accelerating digital transformation initiatives across industries. As organizations adopt cloud computing, IoT devices, and AI technologies, their attack surfaces expand exponentially. Consequently, cybersecurity investments must scale proportionally to address these growing risks.
Additionally, regulatory compliance requirements are driving increased cybersecurity spending. India’s Personal Data Protection Bill and sector-specific regulations create compliance obligations that require substantial security investments. Organizations must balance regulatory compliance with operational efficiency and user experience.
Furthermore, the shortage of cybersecurity professionals creates additional market pressures. According to NASSCOM, India faces a gap of over one million cybersecurity professionals. This talent shortage increases the value of automation and AI-powered security solutions that can augment human capabilities.
Enterprise Implementation Strategies
Successfully implementing proactive cybersecurity requires comprehensive organizational transformation beyond technology deployment. Organizations must align cybersecurity initiatives with business objectives while ensuring adequate resource allocation and stakeholder buy-in.
Moreover, cultural transformation is essential for proactive security success. Security must evolve from a compliance function to a strategic business enabler that supports innovation and growth. This requires executive sponsorship and cross-functional collaboration across IT, business units, and management teams.
Additionally, organizations must invest in continuous training and skill development. Security teams need expertise in AI technologies, threat intelligence analysis, and incident response orchestration. This skill development enables organizations to maximize their security technology investments.
Furthermore, vendor consolidation strategies can improve security effectiveness while reducing operational complexity. Rather than managing multiple point solutions, organizations benefit from integrated platforms that provide comprehensive protection. This consolidation enables better threat correlation and response coordination.

Industry Expert Perspectives, Keynote, and Panel Insights
During her keynote presentation, Sharda Tickoo, Country Manager for India and SAARC at Trend Micro, emphasized the increasing adoption of artificial intelligence by attackers to speed up cyberattacks, thereby reducing exploit timelines from weeks to hours. She added that defensive AI is developing even more rapidly, allowing real-time detection, automated response, and proactive mitigation. By introducing Agentic AI as the new frontier, she described how intelligent agents can collaborate to provide a single and proactive defense solution. At the core of this initiative lies Trend Vision One™, which is integrated with Trend Cybertron, the cybersecurity industry’s first LLM. Together they offer predictive analytics, risk scoring, and automation remediation functionalities to counter advanced and evolving cyber threats. Nevertheless, despite the revolutionary impact of AI on security operations, Sharda highlighted that human oversight remains necessary for effective governance.
Panel Discussion
The Bengaluru event’s panel discussion provided valuable insights into enterprise cybersecurity strategies. Ratan Jyoti from Ujjivan Small Finance Bank emphasized that true cyber resilience depends on embedding business context into security programs. This approach enables organizations to anticipate threats rather than merely respond to incidents.
Moreover, Karthikeyan Dhayalan from Cognizant highlighted the importance of continuous exposure management using external threat intelligence. Organizations must assess their security posture relative to emerging threat patterns and adjust their defenses accordingly. This external perspective enhances internal risk assessments.
Additionally, Nishikant Panda from Mphasis advocated for security-by-design approaches that create security-conscious organizational cultures. Sustained visibility and measurable awareness programs help embed security into business processes rather than treating it as an afterthought.
Furthermore, all panelists agreed that proactive security requires alignment across cybersecurity, risk management, and compliance functions. This alignment ensures that security initiatives support business objectives while meeting regulatory requirements and stakeholder expectations.
The convergence of artificial intelligence, proactive security strategies, and business-aligned risk management is reshaping cybersecurity across India. Organizations that embrace this transformation will gain significant competitive advantages through reduced security costs, improved threat detection, and enhanced business agility. However, success requires more than technology adoption—it demands cultural transformation, strategic alignment, and continuous learning. As cyber threats continue to evolve, the organizations that invest in proactive, AI-powered security capabilities today will be best positioned to thrive in tomorrow’s digital economy.